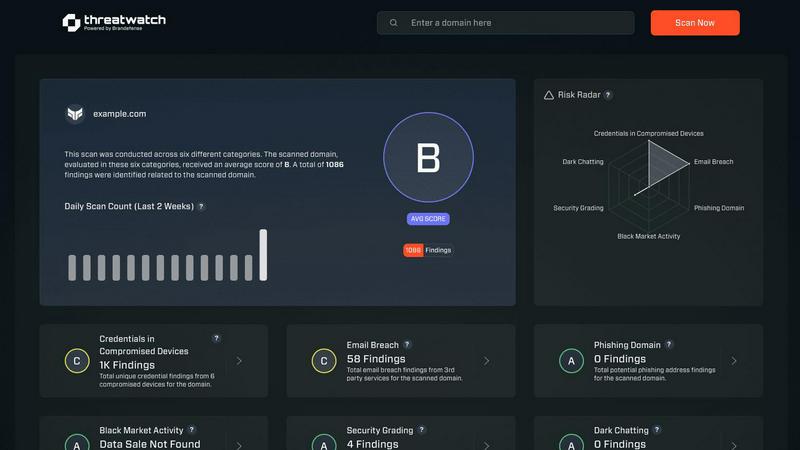
Threat Watch is a unified cybersecurity intelligence platform designed to empower your entire security team with a clear, actionable view of your organization's digital risk posture. It functions as a collaborative hub that continuously analyzes your external assets, vulnerabilities, and exposures across the clear, deep, and dark web. By synthesizing data from these diverse sources, Threat Watch delivers a comprehensive "cyber health" score, enabling teams to move from reactive alert management to proactive risk mitigation. It is built for IT leaders, security analysts, and risk management professionals who need to consolidate their view of external threats and prioritize efforts based on real-world impact. The core value proposition lies in its ability to foster synergy between different team functions—from IT operations to executive leadership—by providing a single source of truth about credentials in breach, compromised devices, phishing campaigns, and dark web exposures, all updated in real-time to accelerate collective response.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
aVenture
aVenture is your collaborative AI platform for in-depth startup research, competitor mapping, and investor tracking.
iGPT
iGPT gives your team a secure API to turn messy email data into trusted, actionable answers.